- What do people use when Telnet is not installed to check a port is open and reachable? I used to use the technique of telnet and know it was there, even if telnet could not interact with the system on the other end.
- Jan 11, 2020 By default, ssh listen on port 22 which means if the attacker identifies port 22 is open then he can try attacks on port 22 in order to connect with the host machine. Therefore, a system admin chooses Port redirection or Port mapping by changing its default port to others in order to receive the connection request from the authorized network.
Well we might as well call this month our SSH month since we are full throttle on SSH! Following our “Reverse SSH Port Forwarding” and “How to Configure SSH Tunnel on Putty”, we thought it would be good to look at securing Open SSH, since security is RDM’s number one priority!
SSH port will be open. If you missed the option during installation or simply just need it later, you can manually install and configure the necessary at the terminal. Step-by-step video guide: Steps to install and enable SSH server on SUSE: Refresh zypper's package list.
When talking about remote access standard, Open SSH has become the norm. It has made other protocols such as Telnet unnecessary since SSH encrypts your connection and passwords are no longer sent in plain text.
Still, using the default installation for SSH can have its own downfalls when it comes to security. When running an SSH server, there are a few easy steps that will considerably increase the installation’s level of security.
Here is our top 10 list for how to secure your Open SSH:
1. Strong Usernames and Passwords
If you have SSH running and exposed to the outside world you will probably notice some log attempts made by hackers that are trying to guess your username and password. A hacker will usually try to scan for port 22 (default port) to discover machines running SSH; they will then try a heavy-handed attack against it. A strong password will help win the fight against an attack! Use RDM Password Generator to generate strong and random passwords and use our list of Forbidden Passwords to prevent anyone from using 123456 or other such nonsense.
2. Configure Idle Timeout Interval
To avoid having an unattended SSH session, you can set an Idle timeout interval. Open your /etc/ssh/sshd_config file and add the following line:
The idle timeout interval you are setting is in seconds (360 secs = 6 minutes). Once the interval has passed, the idle user will be automatically logged out.
3. Disable Empty Passwords
You need to prevent remote logins from accounts with empty passwords for added security. Open your /etc/ssh/sshd_config file and update the following line:
4. Limit Users’ SSH Access
To provide another layer of security, you should limit your SSH logins to only certain users who need remote access. This way, you will minimize the impact of having a user with a weak password.
Open your /etc/ssh/sshd_config file to add an ‘AllowUsers’ line, followed by the list of usernames, and separate them with a space:
Then restart your SSHD service by entering one of the following commands:
5. Disable Root Logins
One of the most dangerous security holes you can have in your system is to allow direct logging in to root through SSH. By doing so, any hackers attempting brute force on your root password could hypothetically access your system; and if you think about it, root can do a lot more damage on a machine than a standard user can do.
To disable your Root Logins, you’ll need to edit the SSHD configuration file. All your SSH server settings are stored in the /etc/ssh/sshd_config file. Open that file while logging on as root and find the section in the file containing #PermitRootLogin in it.
The # symbol (comment) tells the server to ignore anything after it on the same line. Remove the # for the changes to take effect.
Then restart your SSHD service by entering one of the following commands:
You are now safe from brute force root login. If you then need to access root, simply log in as a normal user and use the su command.
6. Only Use SSH Protocol 2
SSH has two protocols that it can use. Protocol 1 is older and is less secure. Protocol 2 is what you should be using to harden your security. If you are looking for your server to become PCI compliant, then you must disable protocol 1.
Open your /etc/ssh/sshd_config file and look for the following line:
Remove the 1, then uncomment it (remove the #). The final line should look like this:
Then restart your SSHD service by entering one of the following commands to apply the changes:
7. Use Another Port
One of the main benefits of changing the port and using a non-standard port is to avoid being seen by casual scans. The vast majority of hackers looking for any open SSH servers will look for port 22, since by default, SSH listens for incoming connections on that port. If it’s harder to scan for your SSH server, then your chances of being attacked are reduced.
You can choose any unused port as long as it’s not used by another service. A lot of people might choose to use 222 or 2222 as their port since it’s pretty easy to remember, but for that very reason, hackers scanning port 22 will likely also be trying ports 222 and 2222. Try and select a port number that is not already used, follow this link for a list of port numbers and their known services.
To change your port, open your /etc/ssh/sshd_config file and add the following lines:
Then restart your SSHD service by entering one of the following commands to apply the changes:
Don’t forget to make the changes to port forwarding in your router and any necessary firewall rules. You will also need to advise your client of any port changes so they know which port to connect to since SSH will no longer be listening for connections on the standard port.
8. Allow Only Specific Clients
If you want your server to be reachable from only a specific IP address on port 22, then you should consider filtering connections at your firewall by adding a firewall rule on your router or update your iptables like this:
With that rule, you are opening the SSH port only to YourIP.
If it is essential for you to open the SSH port globally, then iptables can still help prevent heavy-handed attacks by logging and blocking repeated attempts to login from the same IP address.
The following rule records the IP address of each new attempt to access port 22:
The following rule verifies if that IP address has tried to connect three times or more within the last 90 seconds. If it hasn’t, then the packet is accepted (this rule would need a default policy of DROP on the input chain).
Filtering at the firewall is a tremendously useful method of securing access to your SSH server.
9. Enable Two-Factor Authentication
Your SSH servers should be secured with Two-Factor Authentication configured on it. It is one of the main protections you can add to your SSH servers to protect them from unauthorized access since each user login must tie back to a configured 2FA user. Even if a hacker manages to get a hold of your password or breaks into your SSH server, they will still get blocked by the 2FA. Follow this link to learn more about securing SSH with two factor authentication using Google Authenticator.
10. Use Public/Private Keys for Authentication
Public/Private Keys authentication is certainly more secure and a much better solution than password authentication. Each key is a large number with different mathematical properties. The Private Key is stored on the computer you login from, while the public key is stored on the .ssh/authorized_keys file on each computer you want to login to.
This is particularly important if the computer is visible on the Internet. Using encrypted keys for authentication is useful as you won’t need to enter a password anymore. Once the public/private key-pair authentication has been configured on the server, you can completely disable password authentication; this means that no one without an authorized key will be able to gain access. Even the most inventive hackers won’t be able to interfere or sneak onto a session, and no more cracking password attempts.
Here’s how to create a public/private key pair and install them for use on your SSH server:
Start by generating your key-pair, a public key and a private key. The public key will be placed on the server and you will login with your private key (this needs to be performed on each client machine from which you connect):
This will create two files in your (hidden) ~/.ssh directory called: id_rsa and id_rsa.pub The first: id_rsa is your private key and the other: id_rsa.pub is your public key.
You will then be asked for a passphrase, which is your password to unlock a given public key each time you connect. It is your choice to add a passphrase protective encryption to your key when you create it. If you prefer not to use one, simply press Enter when asked for the passphrase when creating your key pair. Be aware that if you do not passphrase protect your key, anyone gaining access to your local machine will automatically have SSH access to the remote server.
Copy the public key (id_rsa.pub) to the server (the remoteuser should never be root; select the default non-root user as remoteuser):
Then login with SSH and copy the public key to the right place:
Then delete the public key from the server, otherwise the SSH client won’t allow you to login to the server:
And finally, set file permissions on the server:
If StrictModes is set to yes in your etc/ssh/sshd_config file, then the above permissions are required.
When logging in to the server, you will be prompted for the key passphrase (depending on your configuration).
Once you have verified that you can successfully login using your public/private key, you can then completely disable password authentication. Open your /etc/ssh/sshd_config file and add the following lines:
And there you go! Our top 10 steps to harden your SSH installation! We truly hope this will help you with the sudden rise in SSH brute force attacks. Securing SSH is more important now than ever!
Open Port website is a free Open Port Check Tool to check a remote TCP port state – open or close. This tool can be also used to test your router or device for port forwarding.
Please provide a Hostname and a port number to check. The defaults that you see are your IP address and the default HTTP port number 80:
Please check our newOpen Port YouTube Page
Watch the video, like, sub, and request!
Let us know your opinion ->Open Port as a Service
Check other free online tools we have:
- Online Ping Test Tool.
- My IP Address Tool.
- DNS Check Tool.
- Blacklist Checker Tool.
Dentrix dental driver download. Some Well Known Ports
| Port Number | Description |
|---|---|
| 21 | FTP |
| 22 | SSH |
| 23 | Telnet |
| 25 | SMTP |
| 53 | DNS |
| 80 | HTTP |
| 110 | POP3 |
| 135 | DCOM (but not only) |
| 443 | HTTPS |
| 1433 | MS SQL Server |
| 1521 | Oracle Listener |
| 25565 | MySQL |
For a full list of port numbers refer to Wikipedia – List of TCP and UDP port numbers
Free tools for windows
Here are free tools for the Windows operating system. Just download and use!
- PingUI (Ping with user interface)
Open Port Check Tool:
A port is a number that represents an entry to a service that is open to the network.
There are 65535 ports available to use. Some of the ports had been assigned to special service by INAN (Internet assigned numbers authority).
In computer networks, an open port is a port that currently uses (open) by a service. An open port can be used to send or/and receive data over the network.
There are two known types of ports. TCP ports and UDP ports. Open port check tool can check the state of a TCP port.
This can be done by sending a packet using the IPv4 (IP version 4) protocol.
An example can be your web browser on the client-side and a web server as the remote server.
The web server uses the default port 80 for HTTP or port 443 for HTTPS to listen and wait for connections.
Your browser establishes a connection to that port, using a local port. Once it connected they send and receive data between them.
An open port check tool can be used to check if the port is currently open or not on a target machine.
It is like a port test, using this tool you can also detect port forwarding status.
You can also use an open port check tool to remotely check if your server is being blocked by a firewall.
Port Scanner:
A port scanner is a tool that can be used to scan a range of ports.
A more advanced or port checker can scan some address or even a full network searching for ports that are open.
In computer security and hacking it is widely used to search for problematic open ports that suppose to be close or monitor.
An open port is like an open door or a window. With the right knowledge, it is possible to use this port to enter into the remote computer.
Using and running a regular port scan is a good method to find open ports and close them. If an open port is found it is also used to understand why and who open it.
There are some very useful tools that can be used to scan the network address for open ports. Using such tools can even find address inside the organization that needs to be removed.
An example of network ports scanner tool is Nmap. Using it you can scan full subnet. It supports several scan methods like TCP SYN scan and TCP ACK scan.
Advanced usage of the tool can detect what is the service (process) that open the port and the operating system behind this service.
Online port scanner:
Ssh With Port Number
The old art of port scanning is still working. Even thou that today there is a more secure method to close and monitor ports and services in the working environment.
For example. An Intrusion detection system (IDS) can be used to monitor the network.
With the advanced of new tools, an online port scanner tool can be used as a source to scan an environment. Scanning from outside the organization.
An online port scanner is a port scanner like any other port scanner. The only deferent is that it works from outside your network. re: a website – online.
It is a great tool that can be used to check if you have unnecessary open ports on your computer/device that needs to be closed.
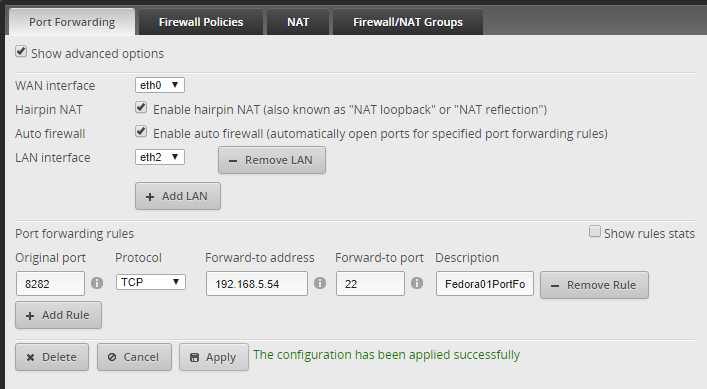
Port forwarding:
Port forwarding allows devices from outside your network to connect to a specific device inside your private network. This is also known as port mapping.
This accomplishes by enabling port forwarding on your router and forward a connection to a special port. The port should be configured to pass the connection into a device in your LAN.
Firewall:
You also need to enable it on your windows firewall or the Unix IP table.
Firewall design for blocking and monitoring inbound and outbound traffic. Firewall monitoring the data against malicious activities.
In LAN (local area network) configuration the inner devices have an IP address that is only available inside the LAN. Most of the time it starts by 10.X or 192.X. The modem/router also has an external IP address that can get out to the internet.
This means that every device that uses the internet actually use the external IP address to surf the web.
The router/DSL modem know who request the external connection and forward the requested data to that device.
This is accomplished automatically by the router.
Once port forwarding is enabled, the device that is outside the LAN will be able to connect into the inner LAN.
This is done by assigning a port in the router or modem to forward state. Once done the incoming data forward to the relevant inner device on the desired port.
Did You Know:
To check a list of ports that currently open on your host and to see what are the IP addresses or the host that your computer is connected to, you can use the built-in command-line tool netstat it is one of the builds in network tools.
Other useful tools:
Open Ssh Port Kali
- Online Ping Test Tool.
- My IP Address Tool.
- DNS Check Tool.
- Blacklist Checker Tool.
Open Ssh Port Windows 10
Have Fun.
